Trump got Trumped
TechnologyOn Tuesday the 27th of October President Donald Trump’s website was hacked by unidentified attackers, with it being believed to be a cryptocurrency scam.
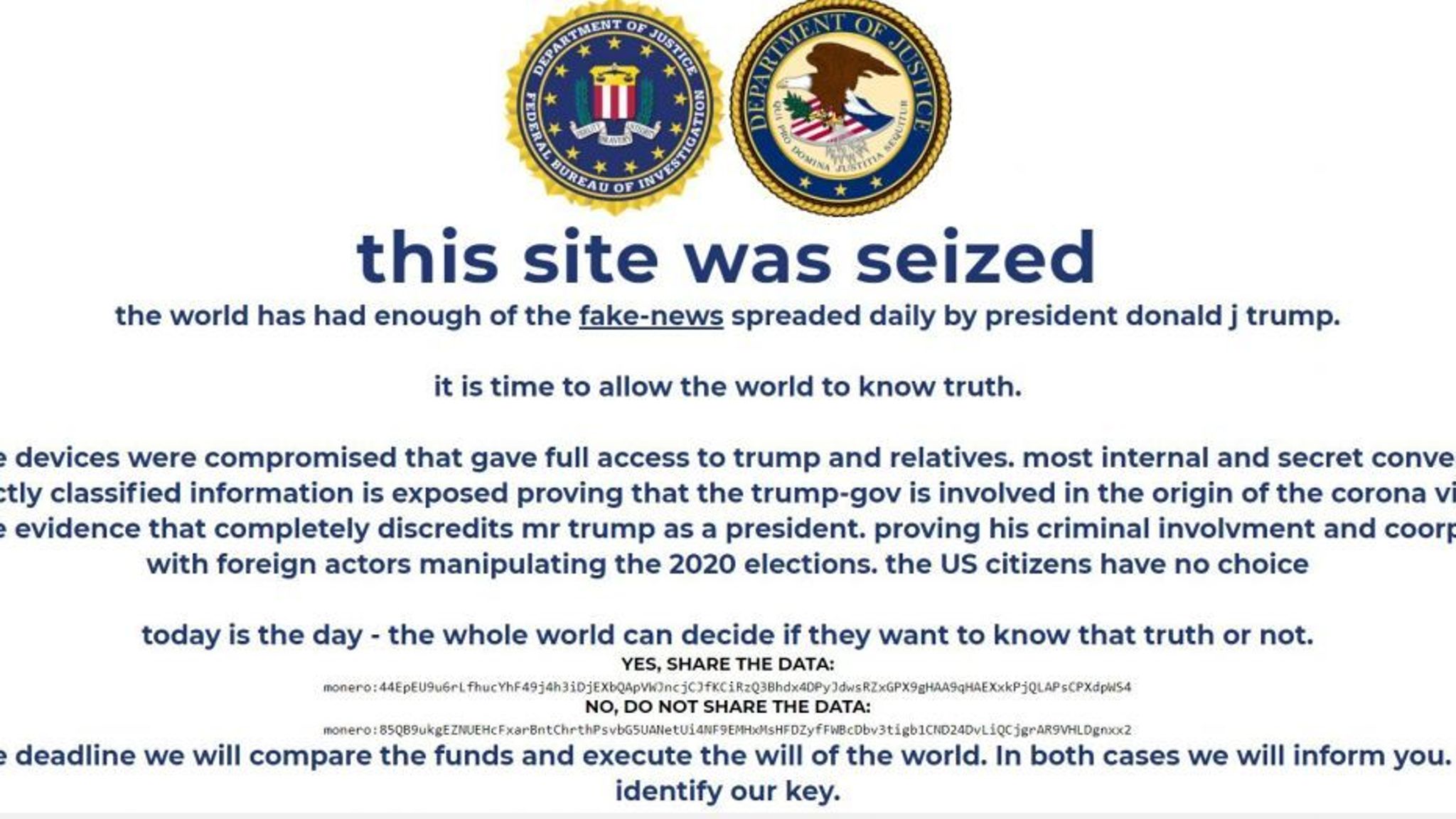
They briefly supplanted Trump’s campaign website with a fake message resembling a Department of Justice notice. “This site was seized. The world has had enough of the fake news spreaded [sic] daily president Donald J Trump”, the message on www.donaldjtrump.com showed.
The hackers left a message declaring that they had compromising information that showed the Trump administration was guilty of “cooperation with foreign actors manipulating the 2020 elections” and “involved in the origin of the corona virus [sic].” The page also included two Monero cryptocurrency wallet IDs urging visitors to “vote” by sending cryptocurrency to the wallets. They claimed that if the first wallet received more cash than the second, they’d release this information.
Trump’s campaign team investigated the breach and a representative said they were working with law enforcement to look into the attack. “There was no exposure to sensitive data because none of it is actually stored on the site,” they said. Although the attack only lasted half an hour, this begs the question of how did this happen in the first place?
The website was made using the ExpressionEngine CMS, which is thought to have very few vulnerabilities. Since the site used Cloudflare as a content delivery network (CDN) the hackers would not have been able to access the site via FTP or SSH unless they knew the Origin IP.
There are two primary techniques that the attackers could have used to access the Trump campaign website. The first being that compromised credentials were used to login to the ExpressionEngine system that was being used. There is a high probability that this was the case as both the “Privacy Policy” and “Terms & Conditions” pages displayed a “404 page not found” error hours after the site was restored. This shows that something changed on the CMS, not on Cloudflare.
The second most likely way that the hackers could have gained access is through using compromised credentials to sign into Cloudfare but this is less likely. If an attacker was able to sign into the campaign’s Cloudflare account, they could easily replace the site’s content with the content that is on their own hosting account. This would also explain how the campaign team was able to gain back the original content so quickly.

No matter how the hackers managed to gain access, if Trump’s campaign team had 2-Factor Authentication enabled it would have prevented this from occurring. This event is a great reminder that it is vital that everyone enables 2-Factor Authentication not only on their website’s administrative panel, but on every service that offers it as this is another level of protection.
Want to learn more about website security? Talk to one of our technical experts about how we can secure your technical infrastructure.
Photo by Nahel Abdul Hadi on Unsplash



